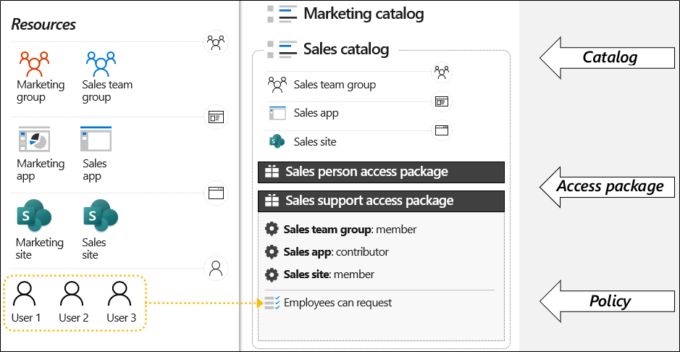
By automating access request procedures, access assignments, reviews, and expiration, entitlement management is an identity governance tool that enables businesses to manage identity and access all stages at scale. Business employees require access to various groups, programs, and SharePoint Online sites to do their jobs.
The management of this access is difficult due to shifting needs. Users require higher access permissions, or there are new apps introduced. When you work with outside groups, the situation becomes more challenging. They will need to be made aware of the apps, groups, or websites your organization uses, and you need to know who in the other organization requires access to your organization’s resources.
Managing access to resources and information becomes more crucial as firms expand and change. The Commercial Entitlement service becomes important in this situation. Controlling access to resources and information based on established norms and guidelines is the process of entitlement management. When done effectively, it may assist firms in enhancing security, raising productivity, and cutting expenses. Here are some best practices and pointers for maximizing its potential.
Understand Your Company’s Requirements Thoroughly
Any system or process, including entitlement management, must be implemented successfully to make effective decisions. These actions can assist.
- Stakeholders should be identified and included in the requirements-collecting process.
- Establish objectives and goals to direct the process.
- Do a needs assessment to find gaps in the current systems.
- Engage end users to learn about their unique systems, apps, and data access demands. Then, consider their feedback and insights to ensure the solution satisfies their needs.
- To stay compliant, identify your sector’s regulatory and compliance standards and ensure your entitlement management system complies with them.
- Assess integration requirements to decide how user entitlements and permissions will be coordinated between systems and consider scalability and flexibility for upcoming integrations.
- To provide accountability and efficient monitoring, define reporting and auditing capabilities from the entitlement management system.
- Sort needs into must-have and nice-to-have categories for first execution based on their importance and business effect.
- Use this material as a guide to define and validate requirements to achieve agreement and comprehension during the implementation process.
- Review and update business requirements often, maintain regular contact with stakeholders, conduct routine evaluations, and customize systems to meet changing demands.
Clearly State Your Policies And Guidelines

Clarify your policies and procedures for access to resources and information once you have determined your business requirements. This entails creating access levels, roles and duties, and policies for giving and revoking access. Here are some key elements to consider when establishing these policies:
- Role-Based Access Control (RBAC) uses established roles to allocate access privileges, ensuring that individuals are given the proper access depending on their job duties.
- Establish privileges and access levels to guarantee a regulated and standardized process for allocating entitlements.
- The principle of Least Privilege (PoLP) focuses on offering users the minimal rights required to do their duties, lowering the possibility of unwanted access or resource abuse.
- Establish a defined procedure with steps, supporting paperwork, and people in charge of authorizing requests for resource access.
- Regular access review processes are crucial to ensure entitlements are still relevant and up to date and recertify entitlements to conform to current business requirements.
- To preserve the integrity of entitlement management across the user lifetime, establish methods for providing and de-provisioning user access.
- Establish procedures for the safe processing and storing of login information, as well as strong password requirements and multi-factor authentication (MFA) implementation.
- Sensitive information should be protected by using data categorization, access controls, and encryption, among other measures.
- Build rules and processes, identify, notify, and respond quickly to security issues linked to entitlement management, and build escalation channels.
- Ensure that entitlement management procedures abide by industry laws, incorporate compliance requirements into policies and norms, and conduct audits to verify compliance.
Establish A Reliable Method For Managing Entitlements
A strong entitlement management system must be in place to handle entitlements successfully. This system must be capable of enforcing regulations and guidelines, providing real-time monitoring and reporting, and integrating with other security programs. Here are some key considerations when implementing such a system:
- Consider the needs, budget, and technology stack while evaluating the entitlement management system.
- Access should be granted, and violations must be reported, as the system should be able to enforce access restrictions and guidelines.
- The system should provide a simplified protocol for requesting and authorizing resource access.
- The entitlement management system should automate user provisioning and de-provisioning procedures for effective access control.
- Real-time monitoring and reporting are essential to identify security concerns, stop illegal access, and uphold compliance.
- Centralized entitlements administration is made possible by integration with Identity and Access Management (IAM) Systems which also lowers administrative burden.
- Support from the Segregation of Duties (SoD) helps stop fraud, mistakes, and unlawful activity. The system must be scalable to support future expansion and provide top performance.
- In addition to providing methods for authentication and authorization, encrypting sensitive data, and supporting compliance needs by producing audit logs and allowing compliance audits, the entitlement management system should conform to industry best practices and security standards.
- To enable the effective deployment of the entitlement management system and to optimize its advantages, provide system administrators, users, and stakeholders with training and assistance.
Review And Revise Regulations Regularly
The administration of entitlements is a continuous process that has to be reviewed and updated often. This entails checking that policies and guidelines are still applicable and effective and revising them to handle new risks and evolving company needs.
To guarantee compliance and alignment with business needs, establish a review plan, keep up with industry trends, track security incidents, and theft, get stakeholder input, and analyze business and regulatory changes. Review policies and regulations regularly, keep up with market developments, monitor security incidents and theft, get stakeholder input, and evaluate business and regulatory changes.
To guarantee that security procedures are current and effective, policies and regulations for entitlement management must be regularly reviewed and updated. As part of this, carrying out a gap analysis, working with the legal and compliance teams, communicating policy updates, offering training and awareness programs, documenting policy changes, and maintaining a shared database or knowledge base are necessary. This aids businesses in adapting to challenges, market norms, and operational requirements while upholding compliance and reducing risks.
Provide Instruction And Training

Finally, it’s critical to educate and train staff members on proper methods for entitlement management. Doing so may guarantee everyone knows their duties and prevent unexpected or intentional security breaches.
It’s crucial to identify the training program’s target audience so that the training material and delivery strategies may be adjusted to the audience’s demands. Establish learning goals that align with the objectives of entitlement management procedures. Create educational materials that address important elements of entitlement management. Describe the policies and regulations that govern entitlement management. Share the duties and tasks of the various stakeholders in entitlement management.
It emphasizes the least privilege principle and the significance of adhering to access control policies and demonstrating the tools and processes involved in entitlement management. Additionally, it should promote security awareness, incorporate interactive exercises and simulations, assess learning outcomes, and provide ongoing refresher training to reinforce best practices and keep staff informed of any policy or process changes.
Quizzes, knowledge tests, and scenario-based evaluations should also be incorporated into the training session to see how well the staff comprehends entitlement management ideas. The training program should also offer regular refresher training to remind participants of appropriate practices and keep them informed of any changes to procedures or policies.
Conclusion

Businesses may strengthen security measures, increase productivity, and optimize resource allocation by controlling user access well. This will eventually affect better functional effectiveness and lower costs. A comprehensive approach to entitlement operation includes the following.
- Prioritizing a clear understanding of business conditions.
- Developing strong programs and rules.
- Enforcing a reliable entitlement operation system.
- Reviewing and streamlining programs constantly.
- Offering thorough training and education.
By using these strategies, businesses may use entitlement operations to cover their means, reduce risks, and promote success in today’s changing digital environment.









